Pirate,
in many Windows 10 or MDM workshops, we come back to the point that we discuss how clients or devices will be connected with our on premise environment in future. Of course we then talk about Azure Active Directory. Reason enough that we deal with it here once.
In general I can tell you, that all Microsoft Online Services handle authentication via Azure AD (AAD). So whether you are using O365 (Exchange Online, SharePoint Online, etc.) or services from Azure (OMS, Azure Remote Apps, etc.) – the authentication process is always handled via Azure AD.
All things first: There are three models or editions of Azure Active Directory:
- Free
- Basic
- Premium
For a detailed overview, on which feature is available in which version you will find more information here: Azure Active Directory editions and here: Azure Active Directory Pricing
So here is the scenario:
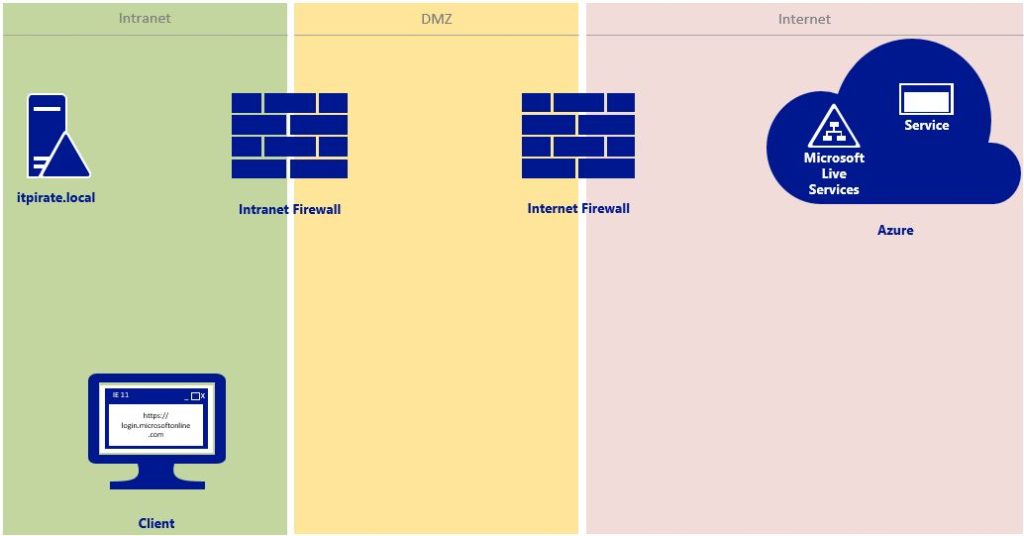
The user of the Windows 10 client wants to use an Azure service (SaaS scenario). He opens up his browser and types the URL: https://login.microsoftonline.com
He reaches the Microsoft Azure portal and has 3 options from here:
The authentification via
- Microsoft Live ID
- Cloud Identity (@[Tenant].onmicrosoft.com)
- Hybrid Identity (@Domain.com)
So this means we have three account types or three logon procedures, right?
The authenticatin process via Microsoft Live ID.
How you probably can imagine everything happens at Microsoft here. This means there is no credential transfer with the on-premise environment.
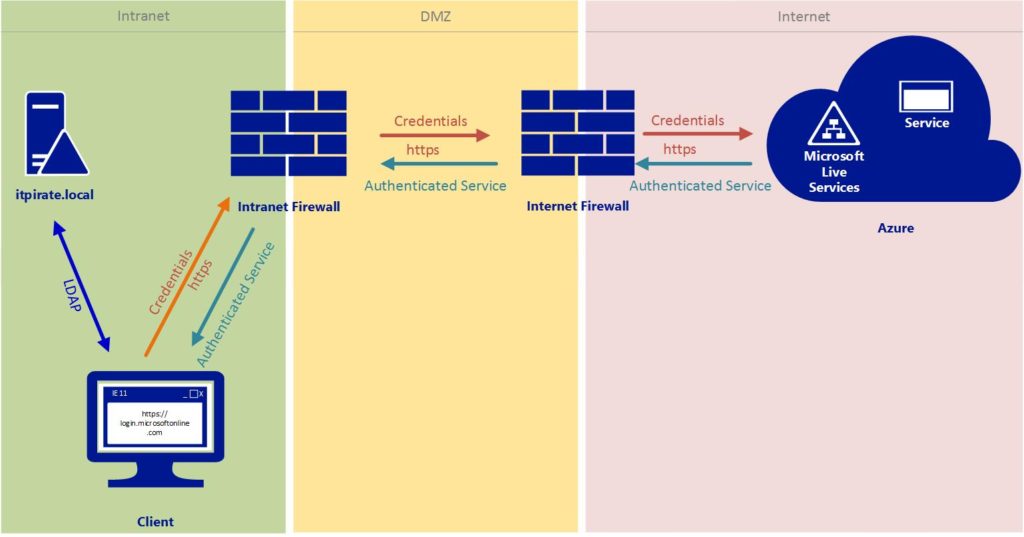
The authenticatin process via cloud identity
In the model of the cloud identity users are created and managed entirely using the O365 admin center.
Advantages of this scenario:
- the Azure AD Domain Services can be used to manage access to resources within the Azure Services
- the complete update management of Active Directory services is managed by Microsoft – you don’t have to take care for that
- the environment runs independently of the on-premise environment and provides high availability / reliability
- it will not require any additional infrastructure
Disadvantages of this scenario:
- standalone password (no sync with the local domain possible)
- authentification is also independently (no single sign on possible)
After the successful authentification, the requested service can be used.
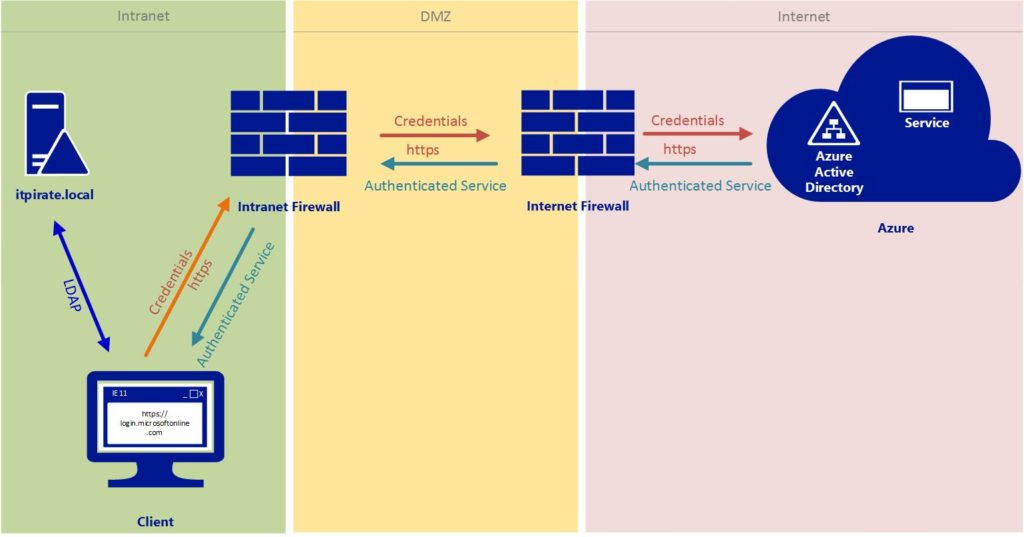
The authentification process via hybrid identity
The hybrid authentification process is divided into two models:
- synchronized identity
- federated identity
For both logon scenarios Microsoft tools such as (DirSync, Azure Active Directory Sync, Azure Active Directory Connect) can be used. In our example, we will start with Azure Active Directroy Connect.
With a synchronized identity the user identity is created and maintained in the local Active Directory. The defined user attributes will be synchronized between the local domain and Azure AD. Depending on the configuration, the data usually gets synched from local AD to Azure AD only (excluding the scenario Azure self-service portal with password reset scenario). With AAD you have the choice to synchronize passwords. However you do not transmit passwords in plain text, much more encrypted password hashes are send.
Advantages of synchronized identity:
- high availability – even when the connection to the on-premises environment is down, you can use the cloud application
- compared to the cloud identity only one user identity must be maintained (less overhead)
- the implementation is simple
Disadvantages of synchronized identity
- no single sign on possible
- synchronization caused delays included
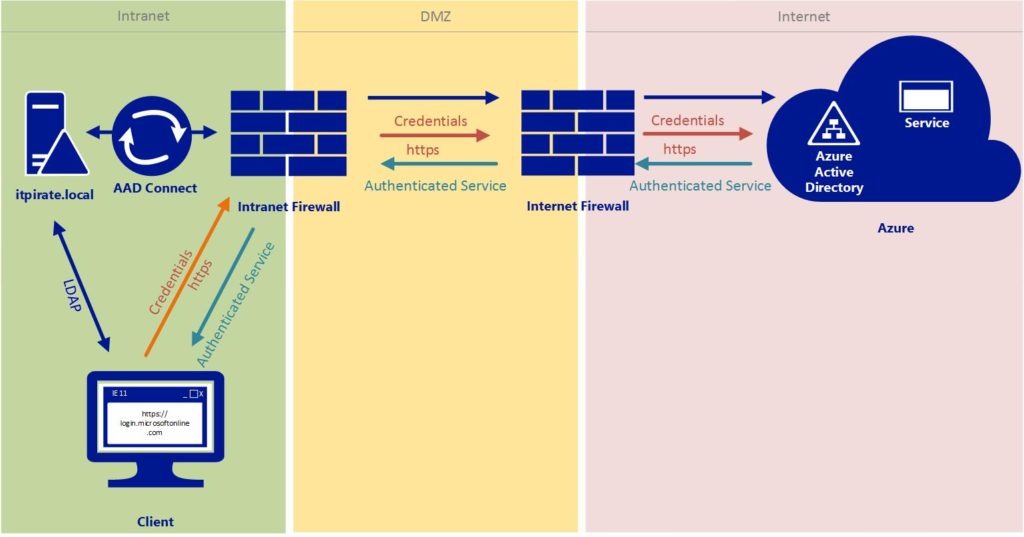
With a federated identity the user identity is created and managed on a local Active Directory Server. As with the synchronized identity the user attributes are synchronized to Azure Active Directory. The difference between the two methods is the handling of passwords, since we are working with Active Directory Federation Server (ADFS) here. This means that the authentication to the cloud service (eg. Office 365) will be forwarded from Azure AD to our local identity provider which is ADFS.
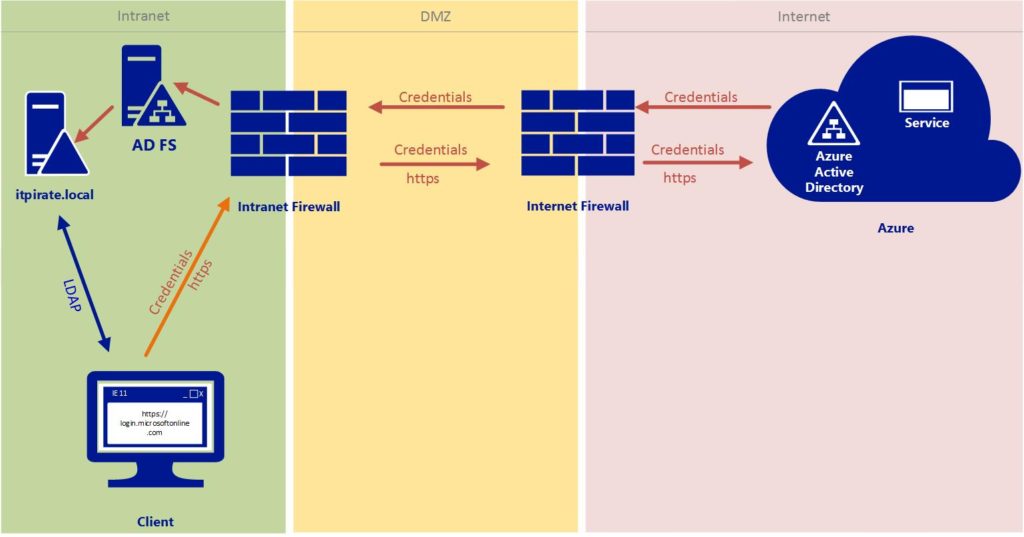
ADFS checks the data in the local Active Directory. Once this process is successfully finished, ADFS creates a valid token and sends that token back to Azure AD, which accepts authentification and allows the user to proceed.
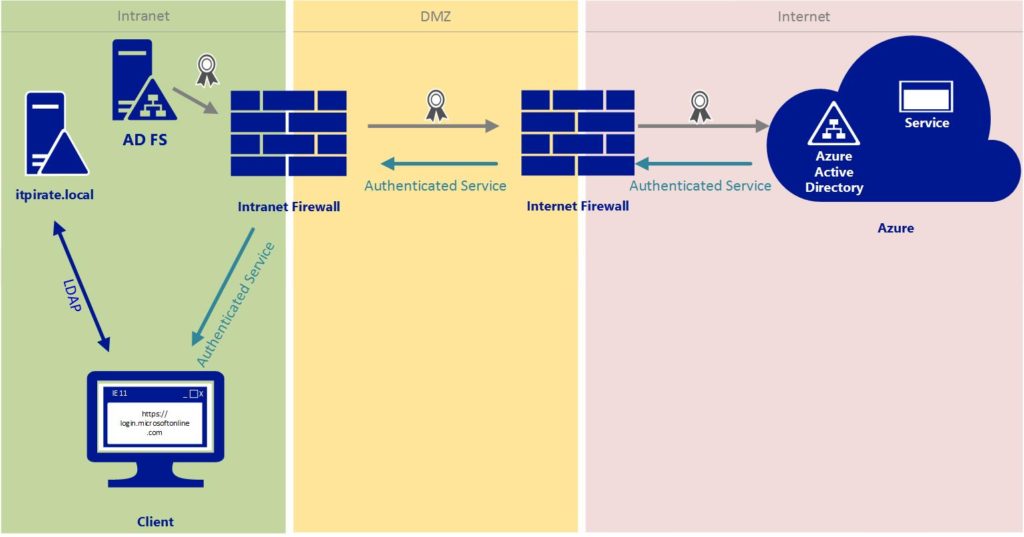
Advantages of federated identity:
- single sign on
- no transfer of passwords (hashes)
- no delay through preceding synchronization
Disadvantage of federated identity:
- higher complexity
Got it?
Cheers,
*Cpt.

Frank
I’ll right away seize your rss feed as I can not in finding your email subscription hyperlink
or newsletter service. Do you’ve any? Kindly permit me recognise so that I could subscribe.
Thanks.
Captain
Hi Frank,
here is the RSS feed: http://it-pirate.com/?feed=rss2
Cheers
Alex